Least Privilege with the Least Headache
Implementing least privilege and removing unnecessary admin rights is hard, but it’s critical to keeping networks secure. With a steady stream of zero-day exploits and novel security vulnerabilities appearing every week, least privilege is a key part of a comprehensive cybersecurity posture for organizations large and small.
But successfully implementing least privilege is hard. Apps like AutoCAD, QuickBooks, and even Microsoft Office often assume that a user has admin rights, creating hard-to-solve issues when those are removed. Other apps want to install updates frequently, and don’t provide an easy way to script updates through your RMM tool.
Given the user frustrations and technical challenges for you and your IT team, you may feel that implementing least privilege is impossible for your organization. But what if there was a better way?
VIDEO
What is the principle of least privilege?
In this video, you’ll learn about why the principle of least privilege is so important to protecting against cyber threats. You’ll also find out how to overcome some of the biggest challenges that IT teams face when implementing it.
Years in the Industry
Organizations Served
Managed Service Provider in Virginia
Save time. Save frustration. Save the day with AutoElevate
AutoElevate by CyberFOX is a unique privilege access management (PAM) solution that solves many of the problems that stem from removing local admin rights – without frustrating your users or creating more work for your tech support team. We’ve been using AutoElevate for five years and appreciate the new improvements and features like Blocker and Just-in-Time Admin. How does it work?
Selective privilege elevation – anywhere, anytime
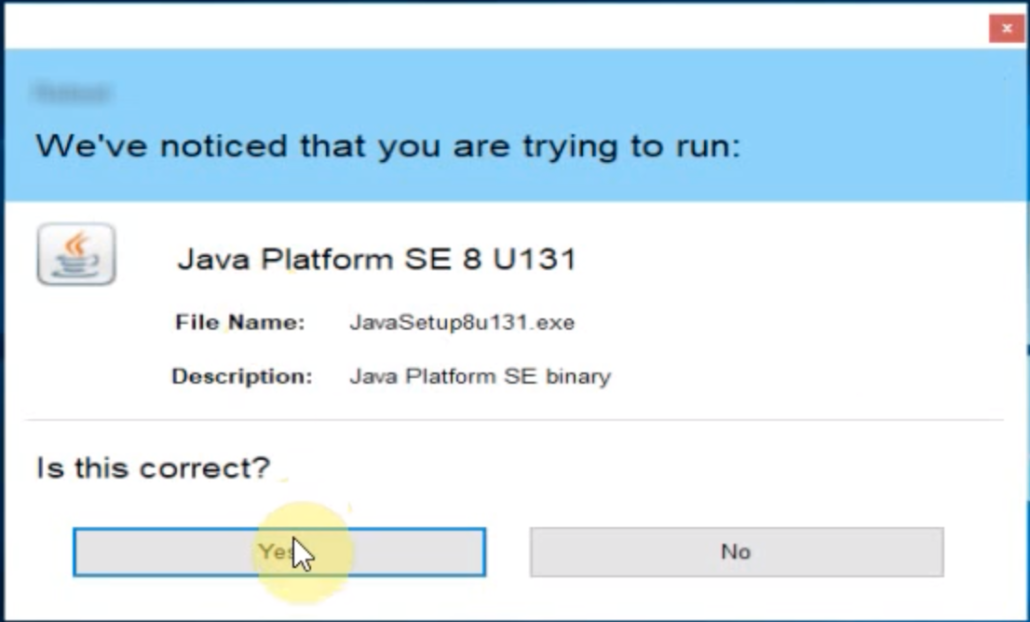
AutoElevate transparently and automatically handles Windows User Account Control (UAC) requests for elevated privileges. Users don’t need to be local administrators or have secondary admin accounts, and your technicians don’t need to make a deskside visit – or even remote in — to enter admin credentials. It works for any function or feature that triggers a UAC prompt, including installed programs or specific program features, EXE or MSI installers, and Windows functions that trigger UAC prompts, such as changing Control Panel settings.
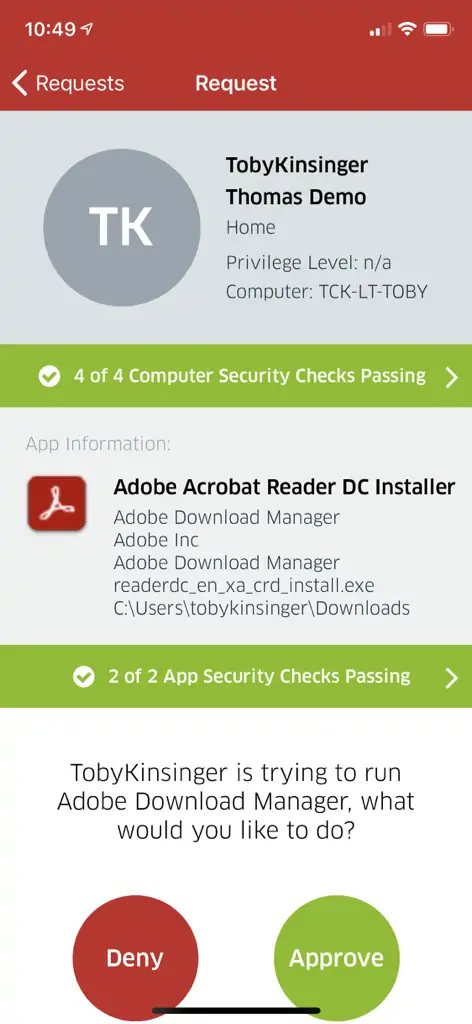
Any UAC prompt will send a notification to technicians’ smartphones or desktops, letting them approve or deny a request immediately. If a technician isn’t available, or the request needs a bit more investigation, a ticket can be created automatically so that nothing falls through the cracks.
Technicians are provided with detailed information for each request, including the software publisher, certificate status, file path, and VirusTotal results. This allows them to quickly approve known-good requests while avoiding malicious ones. Technicians can select whether to elevate using the user’s own credentials, or an “over-the-shoulder” admin account. The authentication takes place locally; admin credentials aren’t stored or transmitted over the network, ever – keeping your information protected.
Powerful automation saves time
In addition to manual approval, rules can be configured to automatically approve elevation requests for known software. Rules can be added in real time based on software vendor, publisher certificates, MD5 hashes, or a combination of criteria. Rules can be scoped to a single machine, a group of computers, or your entire organization to ensure that business-critical software works every time without waiting for approval.
Or, requests can be automatically denied using the same rules and scoping. This protects your systems from unwanted or insecure software without bothering your technicians each time.
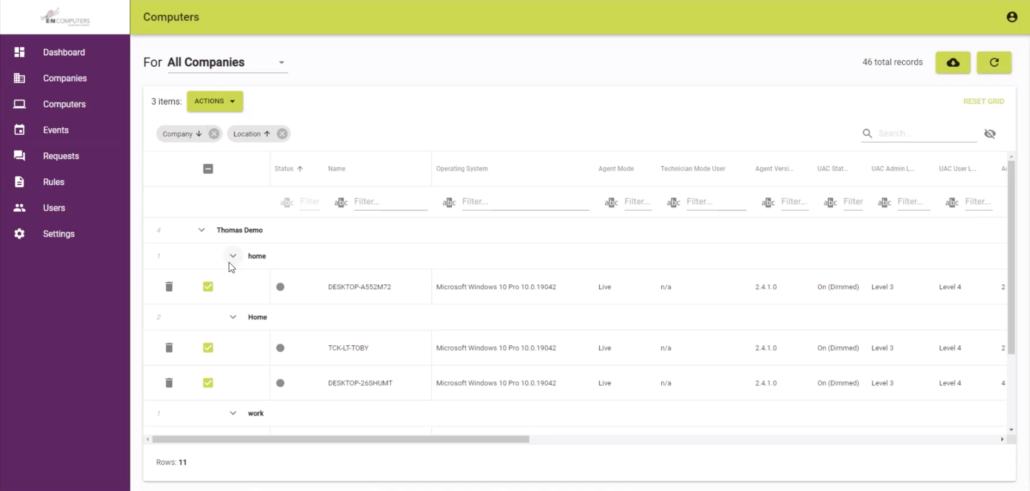
AutoElevate admin console
Get a bird’s-eye view with auditing and reporting
AutoElevate logs information about every UAC elevation request that’s made on your network. Use Audit Mode prior to implementing least privilege to see who has admin rights and which software is requesting elevation. Then, use AutoElevate to ensure that UAC is enabled across your network and that no unnecessary local admin accounts are in use. AutoElevate can even remediate computers automatically by removing user accounts from the local administrators group and turning UAC on.
Any suspicious elevation requests can be investigated using detailed logs. Find out what elevation attempts were made by whom and when.
More control means more security
Removing admin rights and monitoring requests for elevated privileges protects your systems, data, and users from many serious security threats, including:
- Ransomware, spyware, and malware: Many malware strains require tricking the user into running untrusted software, entering admin credentials, or approving a UAC request. AutoElevate gives your team the power to review all requests for elevation alongside detailed security information, preventing infections before they happen.
- Unwanted or illegal software: AutoElevate can keep your users focused on work by preventing the installation of non-work-related programs such as games and media applications. And you’ll find out if anyone tries to install pirated software – before it turns into a security risk or legal liability.
- Shadow IT: Unapproved or insecure cloud collaboration apps present a major risk of data loss, whether accidental or intentional. Find out about the use of these apps before they develop into a problem for your organization.
AutoElevate admin prompt
Secure vs. user-friendly: Mutually exclusive?
With all the security that AutoElevate provides for your network, it must be a pain for users to deal with. Right?
No! In addition to its powerful security features and ease-of-use for technicians and administrators, AutoElevate provides a dead-simple experience for your end users.
AutoElevate runs in the background as a lightweight (<40 MB RAM) agent that most users will never notice. When a user attempts an action that requires UAC elevation, that’s when it jumps into action. If the action or program has been pre-approved by your team – for example, launching a line-of-business application – the UAC prompt will immediately disappear and the action will continue, with no further interaction needed from the user or technician. If the program or action does not match a pre-approved rule, the user will be shown a fully customizable dialog asking whether they would like to request approval. If so, your technicians are immediately notified. If approved, the user will be notified, and the action will continue. If the request is denied, the user will receive a notification explaining how to contact your support team if more information is needed. If a request has been denied by a rule, the user will receive a similar notification explaining that the software or action has been blocked, along with contact information to get help.
AutoElevate Compared to Other Least-Privilege Approaches
You’ve probably tried one or more of the following approaches to managing administrative privileges on workstations. With the AutoElevate user experience described above in mind, think about how it compares to these scenarios:
- No Privilege Management: Without privilege management, anyone is free to run whatever software they’d like. While this is certainly the easiest approach to start with, it only takes one malware infection to see the inherent risks of giving users admin rights.
- Secondary Admin Accounts: One common approach to least privilege is to assign users a secondary account with admin rights. While this solves the main issue of least privilege, it can create many others. For one, it means another username and password for users to remember. It also provides no oversight for how admin accounts are used. A user could easily use their admin account to install unwanted software or be tricked into entering admin credentials by malware.
- Call the Help Desk: Another approach is to only allow the IT team or help desk to hold local admin rights. However, this means that users must call the help desk every time they need elevated privileges. While this might not be a problem if it happens infrequently, users who regularly need admin rights will quickly become frustrated – as will your technicians.
How much does AutoElevate cost?
AutoElevate is available from E-N Computers as a standalone service or as part of our managed or co-managed IT services. It is priced per workstation/per month with a one-year minimum term.
AutoElevate + Managed IT Services
Need a bit more help with your IT than just privilege management? Our managed and co-managed plans are perfect for businesses with 10-200 employees and zero or one IT staff. AutoElevate is available as an add-on to any managed plan for a low monthly cost.
When you add on AutoElevate to a managed services plan, our team will take care of the day-to-day operations, including approving or denying requests, setting up automated rules, and investigating suspicious activity.
To learn more about our managed IT plans, head over to our Pricing page.
AutoElevate for Enterprise
We offer AutoElevate as a standalone service to organizations with 25 or more workstations.
Try before you buy
Contact us to get a fully functional trial of AutoElevate in your own environment — up to 200 workstations — for 14 days. You’ll be able to make sure it is compatible with your software and tools and even get started building automatic allow/deny rules. Your trial can convert directly into your production environment, so you won’t waste any time in securing your systems against the latest threats.
Get the help you need
When you buy AutoElevate through E-N Computers, you’ll get up to four hours of setup and training time.
How can we help?